
Internet Of Things (IoT) is arguably one of the most important technologies of this century. It is driving us to a rapidly digitized world. The hype around IoT has been around for some time, and a common phrase that one often hears was, “We will have 1 billion connected devices.” This was flying around during the 2013-2015 time frame a lot, but not any more.
As with any technology or innovation, the hype comes before its market adoption.
The hype eventually dies out either because there was never a demand for the product, or the market just caught up to the hype. In the case of IoT, the demand overtook the hype.
To put things in perspective, the projected connected devices for the year 2019 was 8.3bn against the actual 9.5bn[source]. This number does not include our phones, laptops, tablets, or similar devices. So yes, a mammoth surge is being witnessed in the number of things that are getting connected starting from our conventional microwave, fans, lights and speakers to more complex industrial automation and monitoring equipment to medical equipment.
The early adopters of new innovations have typically been in the industrial space which is true for IoT as well, where most of the action is taking place.
Let us take India for instance. The adoption rate of IIoT (Industrial IoT) is about 35% in the top 1400 listed large enterprises which clearly makes India a hotbed for IIoT.[source]
But here’s the problem. As with any disruptive technology, industries are facing pushback on adopting IoT on multiple fronts like investments, personnel training, maintenance, and data security.
As more and more industries join the Industry 4.0 bandwagon, and as billions of devices get added to the connected world every year, the data security of these IoT devices can become your Achilles heel of sorts if not given proper attention.
In the following blog, we will briefly cover the importance, monetary impact and challenges in ensuring data security and a general scheme that can be implemented to have a layer of security for these vulnerable devices.
Why is SECURE OTA(Over The Air Update) Important?
Any IoT/IIoT device which is plagued by performance issues on the field will most likely be as a result of a software bug (Critical /Non-Critical), feature enhancements, or difficulty in repurposing the device to meet the current business logic. Most of these issues can be solved by an update of firmware. This is where the OTA process and its security become pivotal.
During an OTA update process, the IoT/IIoT devices are at their most vulnerable state from cyber-attacks and corruption which can render modules useless and result in a significant loss in time/money due to downtime. Depending on the company and type of equipment, this can cost organizations anywhere from $50k (€42.56k)-$150k (€127.69k) per hour for say, a medical device company, and up to $2 million (€1.70 million) for a major outage on an industrial critical asset [source]. Having a reliable and Secure OTA procedure is paramount as the number of connected devices in play are massive and most likely in remote locations.
The Challenges for Secure OTA
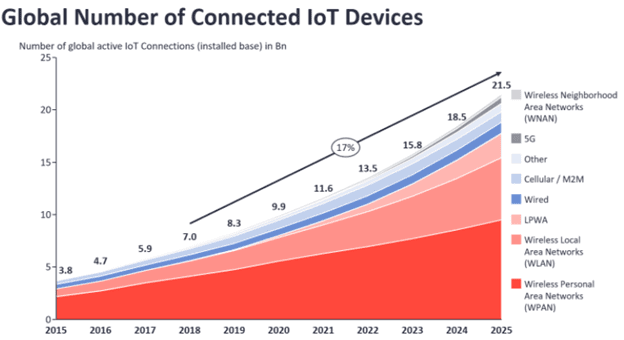
[Source]
As seen above, the highest number of IoT devices are connected through short-range technology (WPAN) that typically does not exceed 100m in maximum range. These include Bluetooth-connected nodes, Zigbee, and Z-wave connected devices.
Many of the SoCs powering these IoT devices are constrained on:
- Memory
- CPU Processing Speed
- Electrical power availability
Other operational constraints are:
- Account for network issues
- Lack of robust fallback mechanism
- Scalability
- Ensuring context-aware updates
Any IoT product planning to have Secure OTA should consider an efficient memory management scheme, ensure SoC has the available resources like an efficient crypto-engine and efficient power utilization.
Keeping up with the needs, many SoC manufacturers have aligned their product to pay special attention to the security challenges faced and have incorporated various innovative IP and encryption schemes. Thus, providing designers the much-needed tools to design a robust and secure system.
Some of the SoCs which are worth noting are the NRF52xx series from Nordic Semiconductors and EFR32BG22 from Silicon Labs and many more. These devices have given special importance to enable data security by providing features like on-chip crypto engine, RNG (Random number generator), etc.
A general approach that can be adopted for any secure OTA system is described below:
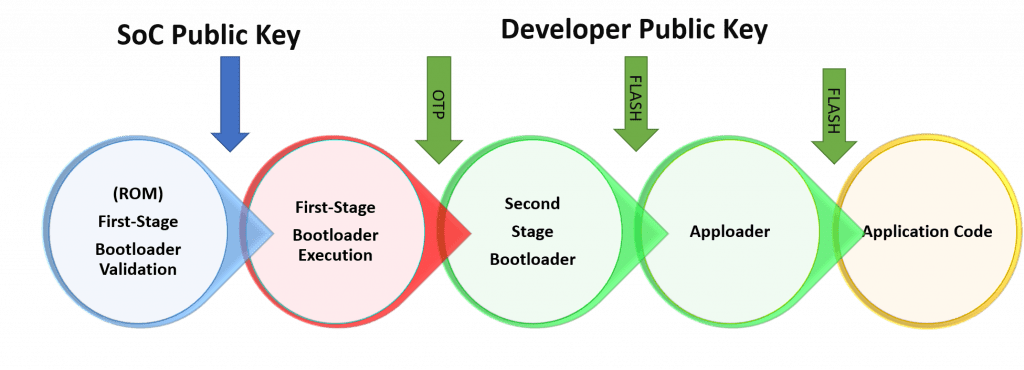
The Developer public keys have three use cases here:
- For First Stage Bootloader to verify the Second Stage Bootloader
- For Second Stage Bootloader to verify the Apploader – or directly the Application
- For Apploader to verify the Application
Key placed in OTP location is made accessible only during the Root Mode by the First Stage Bootloader Execution or the First Stage Bootloader. This provides a true Chain-of-Trust through each stage of the device boot. Keys in the Flash location that are used by the Second Stage Bootloader, the Apploader, and the Application Code. Proper check and algorithm are required in the second stage bootloader to be implemented to avoid erasing the developer keys thereby closing all security loopholes
Depending on the availability of on-chip memory and processing resources we can formulate algorithms to leverage OTP to invalidate keys which are compromised during commissioning or servicing.
At the core of these mechanisms, what we need most is a cryptographic accelerator which will speed data encryption and decryption using a wide range of Advanced Encryption Standard (AES) key lengths and modes. While for authentication and signing operations, the accelerator should support popular elliptic curve cryptography (ECC) curves and hashes. [Ref1, Ref2] .
Conclusion
The growth of IoT/IIoT products is only going to accelerate at an even faster rate bringing with it a whole set of challenges for Device and Data Security in the long run.
Selection of appropriate algorithms, SoC to go with the architecture and application, needs proper deliberation and caution from an overall system design standpoint. Having features like Secure OTA in our product to close the gaping loopholes of security is paramount in this rapidly digitizing world we are in now, to ensure that our privacy and well-being is not compromised.
The post Secure OTA – Advanced Security for the IoT World appeared first on NASSCOM Community |The Official Community of Indian IT Industry.







