It is crucial to recognize the hazards associated with using various software and devices in a world where technology is pervasive in every aspect of our lives. Based on the information provided by the Atlas VPN group, Google, Fedora Project, and Microsoft software had the most vulnerabilities in 2022. Analyzing the specific products, experts in security discovered the most weaknesses in the Fedora, Android, and Windows operating systems.
The existence of more vulnerabilities in a product does not automatically imply that it is less secure. Popular and open-source software products are prone to more vulnerabilities because a larger user base leads to the detection of more exploits.

Google had the highest number of exploits, totaling 1372, among all vendors in 2022. Of all Google products, the Android operating system had the most vulnerabilities, with 897. Additionally, security experts discovered 283 exploits in the Chrome browser, although it did not feature in the top 10 list of products.
The Fedora Project ranked second on the list of vendors with 945 identified vulnerabilities. Among all products, its Fedora Linux product had the highest number of exploits, with 944.
In 2022, security researchers discovered 939 vulnerabilities in Microsoft products. Windows 10 and 11 each had over 500 exploits, while the number of vulnerabilities in the Windows Server OS, from 2012 to 2022, ranged from 414 to 553.
Debian products had 887 exploits, and their Linux operating system had 884 vulnerabilities, securing the third position among all products. Furthermore, Apple had 456 exploits in its products, with macOS having 379 vulnerabilities in 2022.
Cybersecurity writer at Atlas VPN, Vilius Kardelis says, “As the reliance on technology continues to increase, so does the threat of cyberattacks. Individuals and organizations must remain vigilant about updating their software and taking proactive steps to protect against cyber threats.”
Severity of vulnerabilities
The Common Vulnerability Scoring System (CVSS) is a tool for evaluating the severity of vulnerabilities in computer systems and networks. It assigns a numerical score to vulnerabilities based on criteria such as exploitability, impact, and complexity.
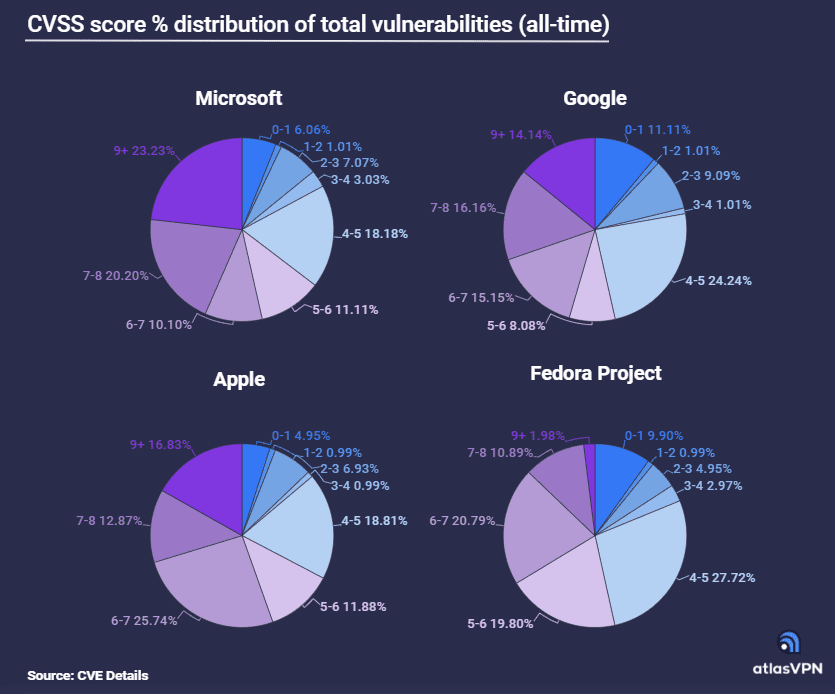
In Microsoft products, over a fifth (23%) of vulnerabilities are rated 9+ on the CVSS scale. Additionally, 20% of exploits are given a score of 7-8.
Exploits in Apple products with a score of 9+ constitute 17% of all vulnerabilities. Furthermore, 26% of vulnerabilities are rated 6-7.
Google ranks third on the list of severe exploits rated 9+, accounting for 14% of all vulnerabilities.
In the Fedora Project, only 2% of vulnerabilities are scored as the most severe, while those rated 6-7 make up 21% of all exploits.
Click here for more details.
Read next: Synopsys report reveals 84% of open-source codebases contain at least one vulnerability








