Second annual report in the row, Nuix Black Report 2018 is a unique work on cybersecurity landscape. It gets into the hackers’ minds and the insights it draws can help enterprises anticipate, detect and be forearmed against cybersecurity threats.
It concentrates on what happens before the breach – the difference maker being professional hackers’ opinions and observations, regardless of the color hat they typically wear.
A report framed from the attacker’s perspective, it has hackers or professional penetration testers as respondents, who filled in the surveys anonymously online or in person during the week of Black Hat, besides Vegas, and DEFCON, the hacker summer camp.
Chris Pogue, Head of Services, Security and Partner Integration, Nuix, wrote in his post, “The Black Report gives you security “awareness in depth” by cutting through all of the noise and misperceptions about cybersecurity that come from only looking at breaches and incidents in the proverbial rear-view mirror”.
The report provides information on:
- What attackers target within breached organizations?
- How long it takes them to breach a network?
- Which industries are easiest to hack?
- Which defense mechanisms are challenging to attackers?
It provides the much- needed insights on hackers of current attacks, their opinion of organizational security posture, and the data types at risk.
Some key questions answered for deeper understanding of the nexus between attacker methodology and defensive posture. Let’s dive deep:
What is penetration testing? How pentesters are different from hackers?
Black market report defines a hacker as someone who accesses computer systems or applications without permission, and executes nefarious activities for destruction or personal gain, whereas penetration testers are those professional hackers who operate within a boundary of a legal statement of work that grants them permission to attack their target.
This piece of paper is referred to as a “get out of jail free card” and is the primary difference between a skilled penetration tester and a malicious hacker. In the absence of this document, pentesters are supposed to be engaged in criminal activity.
However, tools and techniques used by both of them are almost same. But, becoming an effective pentester requires a deep understanding of many technical disciplines including web applications, networking protocols, programming languages, and server operating systems.
How long it takes hackers to breach an organization’s perimeter?
When surveyed, majority of respondents said they can breach most of their target organizations, locate critical value data, and exfiltrate that data within 15 hours. They said that food and beverage, hospitality, retail, hospitals and healthcare providers, law firms, sports and entertainment companies are the easiest to attack.
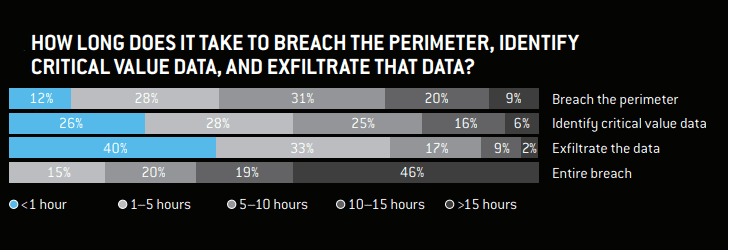
Source – Nuix
28% said that network-based attacks were their favorite to execute, closely followed by social engineering (27%) and phishing attacks (22%). Nearly a quarter of hackers surveyed (22%) were complacent, using same techniques for a year or more.
What are the common security issues that continually reappear?
Nuix investigators noticed that the following themes and practices will be the most concerning future threats.
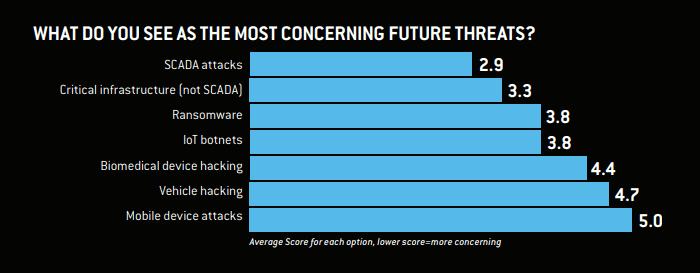
Source-Nuix
Single-factor authentication; unpatched servers and applications; weak or default passwords; antiquated or end-of-life operating systems; overprivileged users; non-work-related activities on critical systems; no network segmentation; and lack of information about crucial aspects are among the reasons that make organizations vulnerable to such attacks.
Who are the hackers targeting you?
The Black Report also shatters another common perception of cybersecurity, that of a teenage hacker living in the basement. The majority of hackers (57%) worked for medium-sized, large, or enterprise businesses. Three-quarters of respondents were college graduates and nearly one-third (32%) had postgraduate degrees.
According to the 2018 Black Report, 34% of the respondents had been hacking for more than 10 years and 78% did not believe that technical certifications were a good indicator of technical ability.
Almost all the hackers surveyed were motivated by curiosity—86% said they liked the challenge and hacked to learn.
What do organizations need to do differently to protect themselves from hackers?
Breaches are often the result of lack of cybersecurity readiness, early detection, or timely response. So, a holistic approach to cybersecurity is required, that means addressing the before, during and after stages of a potential compromise to prevent it from becoming a full-fledged breach.
Here are some quick picks form Nuix report 2018, to help you address the challenges of cyber – attacks:
1. Build a cyber security incident plan with a hacker
Harlan Carvey, Director of Intelligence Integration, Nuix explains, “Whenever organizations sit down to develop their CSIRP (Computer Security Incident Response Plan), one person isn’t at the table: the hacker. As such, the organization evaluates what data to protect and how to go about protecting it from the position of an insider or a business executive. Might it change things if you understood how someone would attack the organization or compromise its infrastructure?”
While developing and implementing a CSIRP, it can be insightful to get an attacker’s view of what constitutes success when breaching an organization. To beat the hackers, you have to think like them.
2. Understand the behavior of hackers and why people commit crimes
Criminological theories explain the behavior of hackers and why they commit crime. You can use these theories to determine the bio-psychosocial aspects of these offenses and develop a clearer understanding of the elements motivating these types of offenses.
Some of them mentioned in the report are:
- Rational choice theory which states that people are rational actors who make individual decisions after carrying out a cost–benefit analysis.
- Routine activities theory highlights the importance of the opportunity to commit a crime.
- Hirschi’s social control theory states that the strength of a person’s bonds with conventional society—much more than the potential punishment if they are caught—dictate whether they are likely to violate laws.
- Strain theory is useful for explaining illegal hacking motivated by money, ego, status, or malice.
3. Create effective security defenses corresponding to the environment
Organizations of all sizes—private and public, can take hackers’ advice and create meaningful, effective defenses that correspond well with their environment.
Security programs that prevent cyberattacks:
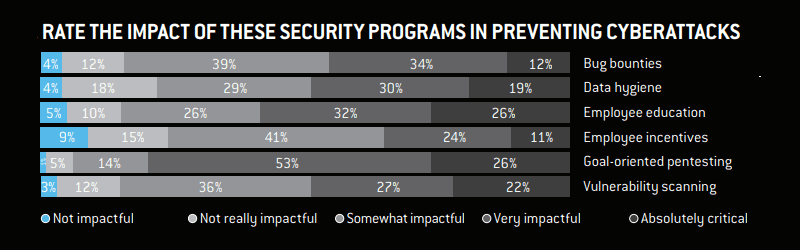
Source – Nuix
Report also suggests security countermeasures that pose a challenge to hackers:
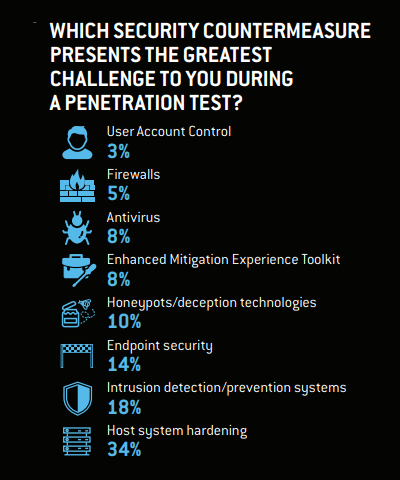
Source – Nuix
When asked, over one-third of respondents (34%) said, host system hardening yielded the best results. It was followed by intrusion detection and prevention systems, and endpoint security. The lowest percentages were firewalls and Microsoft’s User Account Control security framework.
53% hackers also suggested that goal-oriented penetration testing was very impactful or absolutely critical (26%) to an organization’s security posture.
Conclusion
The key takeaway from the 2018 Nuix Black Report is that no industry is safe and secure. So, if you want to protect your organization or your personal devices from joining the next botnet, learn and implement the important lessons from the report to fortify your defense strategy.
Source: https://www.nuix.com/black-report/black-report-2018









My brother suggested I might like this website. He was entirely right.
This post actually made my day. You can not imagine just
how much time I had spent for this information! Thanks!
I’m extremely impressed with your writing skills as well as with the layout on your blog.
Greate pieces. Keep writing such kind of info
on your blog. Im really impressed by your blog.