The Dynamic Malware Analysis System by BitNinja
The COVID-19 outbreak has speeded up the growth of Internet traffic. The number of websites is rising rapidly, and there are more eCommerce businesses than ever. Therefore, the shared web hosting companies are doing a roaring trade. But unfortunately, these are not the only numbers that are growing. Cyberattacks are also on the rise, and no business is safe nowadays. By now, cybercrime is one of the most frequently reported economic crimes in the organizations, making cybersecurity a C-suite and board-level concern.
Today we will talk about how to detect and remove obfuscated malware from shared web hosting servers.
What is Obfuscated Malware?
The obfuscation technique is for hiding the real purpose of a program. The hacker creates a code that is not readable by humans, but the functionality behind it remains the same. So, when you run the program, it will behave like the encapsulated program it was designed for.
How to analyze different types of malware
There are two different types of analysis when we talk about malware: static and dynamic.
Static Analysis
The static analysis includes hash algorithms, string matching, code-based detection, and there is a new, patent-pending technique invented by George Egri (Co-founder and CEO of BitNinja), the source code structure analysis.
| Signature type | Example |
| MD5/SHA2/SHA3 | 5d41402abc4b2a76b9719d911017c592 |
| String match | eval(base64_decode( |
| Code-based | if the first line starts with a lot of space and … |
| SA-MD5 | Full structural match |
| SA-SNIPPET | Partial structural match |
This creates a special structure-based signature from the source code and then does the matching on the structure. This way, no matter how the source is altered, the structure will be the same. It is very similar to how plagiarism checker systems work.
Dynamic Analysis
But jump back to the types of analyses. Besides the static analysis, there is the dynamic analysis. When using the dynamic analysis, you run the source code partially or entirely and observe the program’s behavior.
Deobfuscation

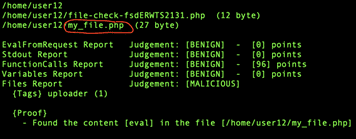
You can see the eval obfuscation in the screenshot here.
One of the behavior analysis methods is deobfuscation. If you find the obfuscation mechanism, you can deobfuscate the code. After that, you can decapsulate the real program and match the deobfuscated source code. But believe me, there are too many different obfuscation techniques. So, it’s not that easy to deobfuscate the code, and there are other aspects that are hard to analyze without partially running the code.
Output
Another technique is from the output when you analyze the output of the program. Most of the time, when you run malware, you can find traces of malicious behavior from the output.
Function Calls

Within the confines of the “Function Calls” analysis, you run the code, and you find which functions are used for malicious activities.
Variable Content

The next one is variable content analysis. This program contains something “phishy”, as you can see in the picture. It’s always suspicious when a source code includes function names like explode and basic commands used to decode interesting variable names.
File Manipulation
It can happen with real files or within a simulated environment to safely analyze file manipulations.
Multi-Path Execution

Finally, you can do multi-path execution when you analyze what would happen if you forced the interpreter into a code branch. This way, you can find locked code parts, and this technique is also quite helpful in discovering malicious behaviors.
How to use these techniques
The old school way
Sandboxing is one way to use these techniques if you have a couple of special servers for that purpose.

These servers can spin up virtual servers, and you upload the PHP file to it, run the code and do the above-mentioned analyzing methods. The disadvantage of this technique is that it takes around 20 seconds to analyze one PHP file. Analyzing all of your PHP files would take a lot of time and eat up too many resources.
The new way
BitNinja has built a PHP simulator. It’s a safe environment where you can partially run PHP files on the server and run all the analyses that we were talking about. With this feature, you can analyze old PHP files on the servers and can discover the most recent zero-day malware, even if they are obfuscated.
How to secure shared web hosting servers?

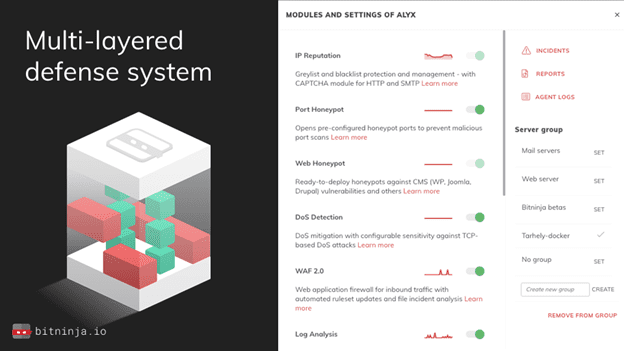
You need different solutions against DoS attacks, brute force, botnets, vulnerability scans, backdoors, and the list is almost never-ending. The best way to secure your servers is to set up a multi-layered defense system that stops the attacks on each layer.
That’s exactly what BitNinja provides. You can install it with a one-line code, and then you have a complex system of layers from real-time IP reputation through honeypots, DoS detection, WAF, log analysis, and of course, malware detection.
About George Egri, CEO, BitNinja George Egri is a cybersecurity and web-hosting expert. He is the co-founder and CEO of BitNinja and the owner of the second-largest shared-hosting company in Hungary, the Web-Server Ltd. Some years ago, they had a lot of customer complaints because of hacked websites. They tried to combine the different tools on the market to secure their servers against the different kinds of cyberattacks, but after a while, it became unmanageable. So, they decided to solve this problem by creating an internal all-in-one solution. This project was the ancestor of BitNinja. They realized that it could be beneficial not just for them but also for the shared hosting industry and the whole Internet. Therefore, they started to establish their resources in BitNinja and make the Internet a safer place.









wonderful article about WordPress security. I had used many security plugins over a while to protect my website. Which plugin is good for WordPress I never understand. My first website was hacked through malware. At that time I was not aware of such things. I tried hard but could not resolve myself. But I learned about some security plugins which help.