Cyberattacks against businesses of all sizes and verticals are increasing. Cybercriminals are generating over $1.5 trillion every year by carrying out the attacks on businesses.
As per Global Market Insights, the cybersecurity market will reach $300 billion by 2024, up from $120 billion in 2017.
This is all the more critical for healthcare and media/entertainment industries because they have the largest surface to protect.
Attackers are targeting healthcare increasingly because healthcare organizations handle the critical data of patients.
In the last two years, 89% of organizations in healthcare have experienced at least one data breach.
Furthermore, the ransomware attacks on healthcare organizations are the highest and are expected to quadruple by 2020.
Whereas, the media and entertainment companies witnessed at least three cyberattacks last year.
CIOs and IT managers are concerned about the security of their companies.
They need to ensure that the company is not only ready to fight major cyberattacks but is also in compliance with regulatory laws like the General Data Protection Regulation (GDPR).
While some companies are protected and secure against cyberattacks, a large number of other companies are still non-protected.
Let’s have a deep dive into what sets apart a protected company from a non-protected one.
Difference between protected and non-protected companies
In this article, we have listed the main differences between a protected and a non-protected company.
#1 SSL Certificate
SSL Certificate has become the basic requisite for website security. It is a security protocol used to create an encrypted and secure connection between a browser and a server.
The websites with an SSL certificate have HTTPS in their URL, whereas, the non-protected websites have HTTP.

So, the first difference between a protected and a non-protected company is the SSL certificate installed on the website.
What is SSL certificate how does it work?
It secures the information submitted by the end-users to the website via contact forms, check-out process, or any other source.
The information submitted to the websites can be sensitive, such as banking details, contact information, credit card details, etc. What SSL does is reduce the risk of this information from getting leaked.
Furthermore, Google has made it mandatory for all the websites to have SSL or it will impact the search rankings. HTTP sites show the ‘Not Secure’ warning to the end-users, which discourages the visitors and scares them.
Also read: What is an SSL Certificate and why is it a must-have for every website?
#2 Protection against ransomware attacks
Ransomware is the fastest-growing attack ever in the history of the internet. It targets small and medium businesses (SMBs), as well as large businesses.
The attackers infect the computers and mobile devices with malicious software, which spreads to other devices in the network.
Following infection, the malware encrypts (locks) the data and shows the users a ransom note.
Attackers demand thousands of dollars (usually to be paid in cryptocurrency) to decrypt (unlock) the data.
The ransom amount for decryption varies, but studies suggest that the average ransomware cost is over $36,000 per attack.
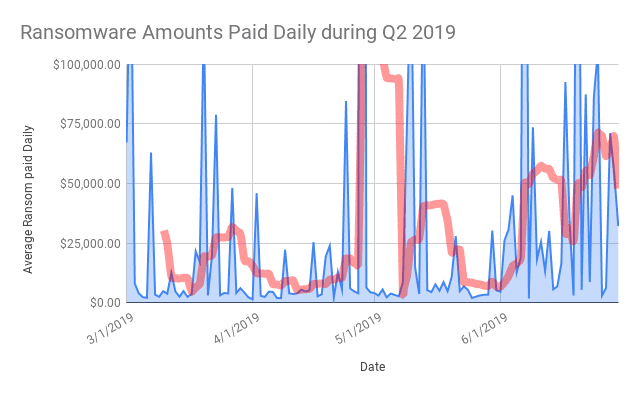
The biggest ransomware attacks in history are the WannaCry and NotPetya.
The WannaCry outage in 2017 affected over 200,000 computers across 150 countries, which costed a huge sum of $8 billion.
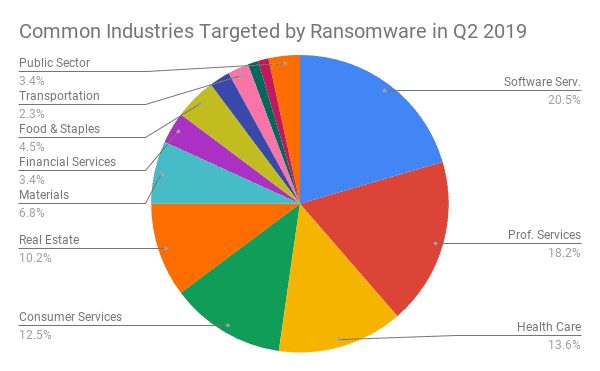
It is worth noting that the IT and healthcare industries are the biggest targets of ransomware.
The organizations in these industries must have the best practices and ransomware attack solutions in place to prevent ransomware and avoid risks and regrets.
How to protect against ransomware? – steps taken by a protected company
The trait of a company that is protected against the ransomware is that it has an active cyber-attack detection and protection solution in place.
#3 Automatic detection of cyberattacks
Organizations in the UK alone faced an average of 146,491 cyberattacks in the second quarter of 2019. That is, one cyber-attack every minute.
Cybercriminals are increasingly carrying out automated attacks on the businesses of all sizes.
While security firms are using artificial intelligence (AI) and machine learning to prevent attacks, the attackers are using it carry out automated attacks. Machines are doing the job.
This makes it easier for attackers to find out the vulnerabilities in the affected systems and then take the things ahead.
Many large cybersecurity firms including McAfee and Symantec predicted that the automated cyberattacks are on the rise in 2019 and the scenario will only worsen in the long run. So, how to monitor for cyber-attacks?
How do protected companies fight automated attacks?
Protected companies use advanced cybersecurity solutions powered by AI and ML. It is important for security solutions to be modern and advanced in order to fight the AI-powered attacks.
The non-protected companies either use legacy security solutions or don’t even use any solution. The legacy tools can’t provide protection against modern cyberattacks.
On the other hand, protected companies invest in cloud and AI-powered security solutions. Acronis Active Protection, again, is the solution here that keeps track of automated attacks hyper-actively.
#4 Cybersecurity Awareness among employees
“A successful cyberattack often starts with the employee.”
Fifty-two percent of the businesses are at risk of cyberattack, from within. The employees are putting the companies at risk because of carelessness, lack of knowledge and training, or intentionally.
IT teams can do their best and have security tools in place for security.
But if the employees are not aware of what to do with malicious things like phishing emails, then the attacks will occur from within the company.
What does a protected company do for awareness?
In protected companies, the IT managers and teams train the employees about the best cybersecurity practices, tips to remain secure, how to detect phishing emails, what to know before clicking a link, etc.

Whereas, the non-protected companies might not be following these practices. They don’t focus on spreading cybersecurity awareness among the employees.
#5 GDPR-countdown notification
According to Article 33 of the GDPR, the companies need to report the cyberattack or data breach to the supervisory authority, within three days of detection.
That’s a real tight window, considering that the companies need to provide details and documents that should include below information:
- Nature of data breach
- Category of attack and the number of data subjects affected.
- Consequences of attack
- Steps were taken to address the attack
It’s not an easy task for the companies to report these things within three days.
Even if they try their best to find the nature of the breach, its category, consequences, and other essential things, it will require them to find the experts, without wasting any time. This can cost them very high.
Do the protected company need to worry about that?
No! the protected companies that are using AI-powered security solutions don’t have to worry about GDPR countdown notification.
#6 Attack analysis and mitigation
To analyze the attack and mitigate it, the companies need to spend an average of around $1.1 million.

Following the attack, the IT teams start working on recovering the data, setting up the systems again, and more such things.
This doesn’t only cost money, but also a lot of time. 37% of companies experienced reputation loss due to a cyberattack.
How do protected companies benefit by preventing cyberattacks?
While the non-protected companies invest their time and money in recovery, the protected companies can focus on productivity and reaching new business heights.
Non-protected companies lose the customers after a cyberattack, and those customers go to the protected ones.
Nobody wants their data or information compromised.
#7 Cloud backup and recovery solution

More than 140,000 hard drives in the US alone fail every week. Forty-six percent of companies don’t even have a backup and disaster recovery plan for their systems, data, and applications.
Why do protected companies prefer a cloud backup solution?
There are several advantages of cloud backup solutions.
They allow businesses to back up and store their data and apps on a remote server.
These data and apps in the cloud remain available, even in cases of system failure, natural or manmade disasters, etc.
The protected companies are aware of the criticality of their data and workloads. They know that the data loss in any circumstance is not affordable.
Hence, they back up all the data and applications to the cloud, which keeps everything secure and protected from outages and disasters.
All the data and apps in the cloud backup can be restored in no time, allowing the company to gain access to the required files easily.
Why non-protected companies don’t have a backup plan?
- They believe that it will never happen to them
- Lack of resources
- They don’t know where to go for help
Many companies, despite knowing the importance of data backup, aren’t using a backup and disaster recovery solution.
In cases of disasters and outages, such companies not only lose their data permanently but also lose customer confidence.
Which cloud backup and recovery solution is right for businesses?
Protected businesses use a hybrid cloud backup solution that is easy-to-use, easy-to-manage, cost-effective, and provides complete data protection.

Are you a protected company?
No business can afford to lose data today. The cybercriminals are finding new and advanced techniques every day and increasingly targeting the businesses of all sizes.
If you are a non-protected company, it’s time for you to become a protected one using the right cloud backup solution.
Origanaly Published on ZNetLive







