In early 2022, many companies around the world asked their employees to come back to work full-time. However, some companies chose to keep a hybrid or remote work setup. This made it difficult for cybersecurity teams to keep different work structures secure because cybercriminals were quick to take advantage of this and launch critical attacks.
Ransomware-as-a-service (RaaS) became popular among malicious actors because it is faster to deploy and can yield bigger payouts. Ransomware operators have begun to target Linux-based systems more often and have also started using new ransomware families in high-profile attacks. In addition, ransomware operators have resorted to both new as well as tried-and-tested methods to attack cloud environments.
The RaaS model
The relationship between ransomware developers and their affiliates has changed because of the RaaS model. Developers can now make money by selling ransomware tools to affiliates. These affiliates then infect people’s computers and share the ransom payments with the developers. This setup gives developers more time to improve their malware, and it also protects them from scrutiny by security researchers and law enforcement. On the other hand, affiliates earn money without doing all the work themselves.
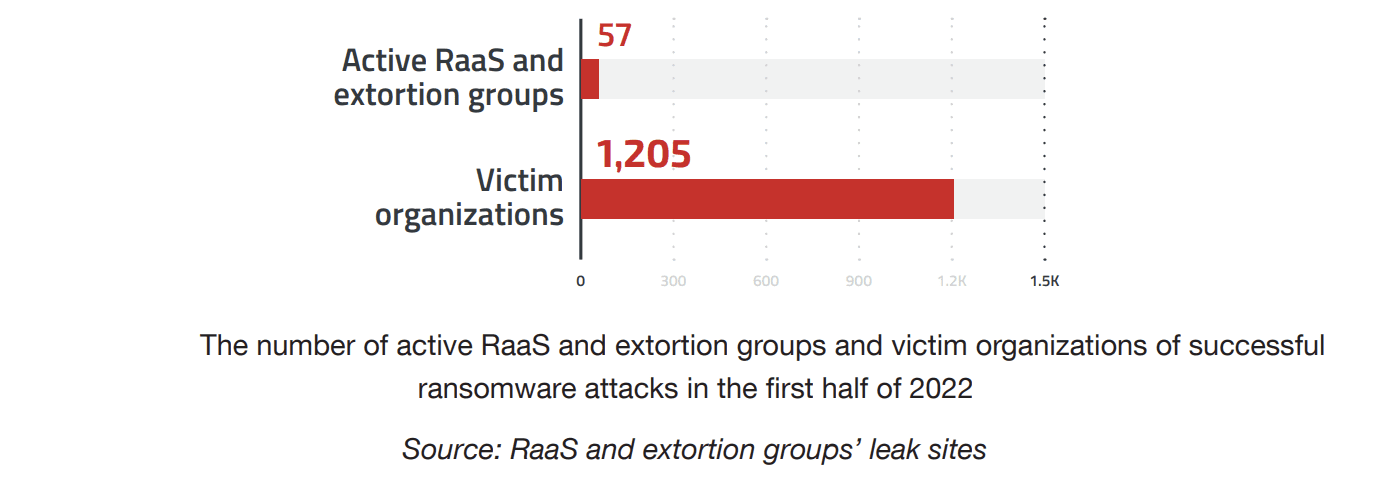
According to a research by Trend Micro, there are over 50 active RaaS and extortion groups. More than 1,200 organizations were hit by ransomware in the first half of 2022.
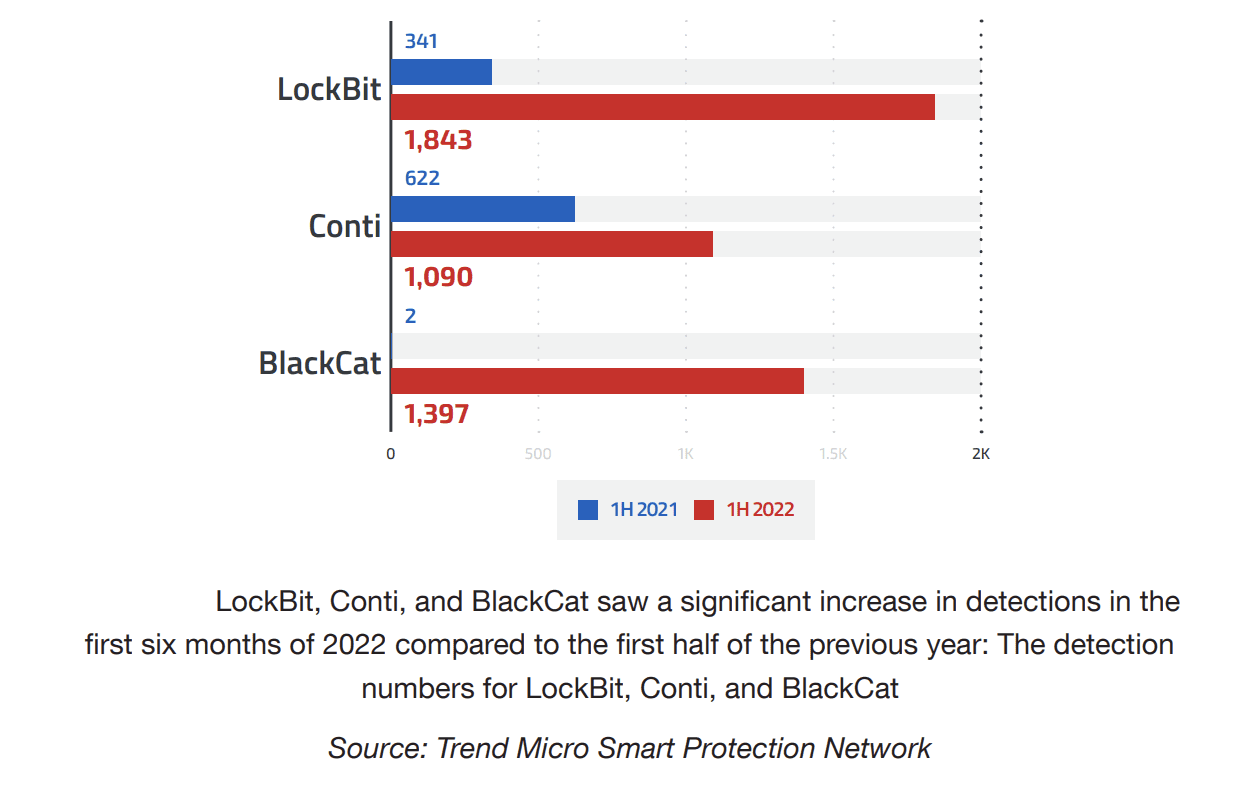
The major players in the RaaS field during the first half of 2022 were LockBit, Conti, and BlackCat. There was also a sharp increase in detections from each of these malware families during this period. Black Cat is a relatively new ransomware, initially reported at the end of 2021. Older ransomware such as LockBit and Conti saw major increases, with LockBit detections growing over five times and Conti nearly twice in the first half of 2022 compared to the first half of the previous year.
Linux Systems are now the prime target for ransomware operators
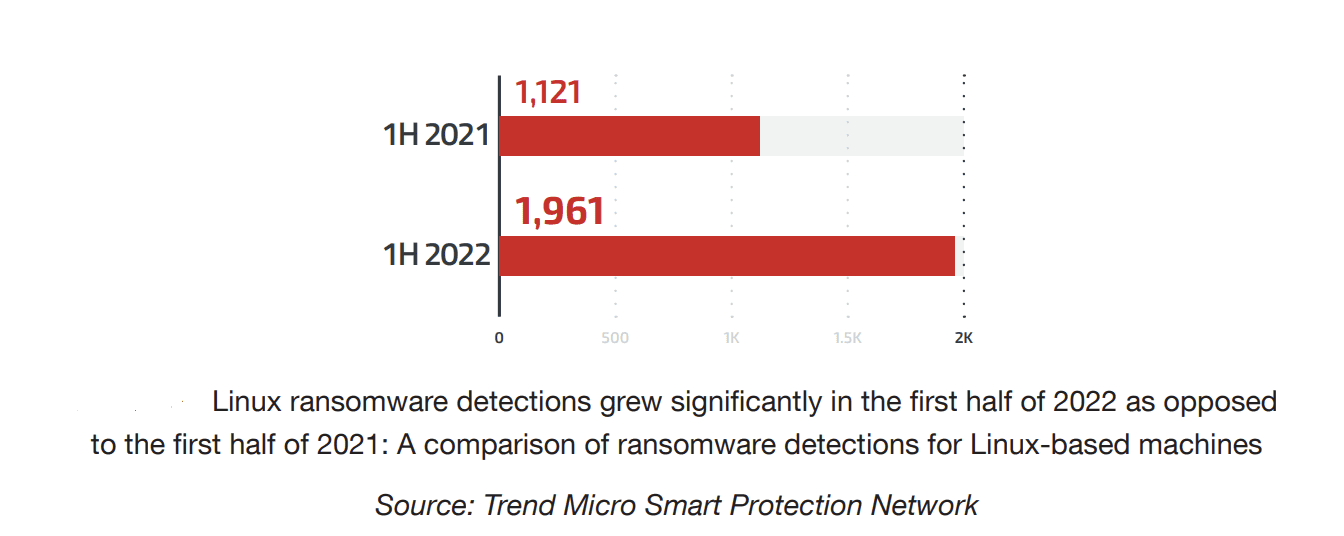
Linux systems have become an attractive target for malicious actors who are looking to expand their reach or have decided to focus on specific types of infrastructure like servers and embedded systems where Linux is expected to see growth in the next few years. In H1 2022, There is an increase of 75% in ransomware attacks that target Linux-based machines as opposed to the first half of 2021.
In October 2021, LockBit’s operators introduced a Linux-based variant, LockBit Linux-ESXi Locker version 1.0, which targets ESXi servers through a combination of Advanced Encryption Standard (AES) and elliptic-curve cryptography (ECC) algorithms for encrypting data. In May 2022, a new ransomware variant by the name of Cheerscrypt was also found that targeted devices using ESXi.
It was observed that the ransomware operators were targeting businesses that could afford to pay high ransom demands. In early 2022, operators of the Black Basta ransomware attacked nearly 50 organizations in a short period. It originated in April 2022, when a user with the name of Black Basta posted on some underground forum that they were looking for corporate network access credentials for organizations in the United States, Canada, United Kingdom, Australia, and New Zealand. The user also mentioned that they would offer a share of the profits to any potential partners.
In the latter half of 2021, the Hive ransomware initiated a string of attacks on the US healthcare sector, in which over 300 organizations were hit in the ransomware’s first hundred days of operation. In 2022, there were attacks launched by Nokoyawa, ransomware with several similarities to Hive like the use of Cobalt Strike and the integration of tools like the anti-rootkit scanners GMER and PC Hunter for evading detection.
The evolution of the ransomware threat landscape indicates that the organizations must have in place strong and comprehensive cybersecurity measures to cover security gaps. Not just this, they also need to educate their employees about cyber threats and the importance of cybersecurity.
Image and source credits: Trend Micro








